Network Hacking: Setting Up A RogueAP With A Raspberry Pi 3 Or 4
The Raspberry Pi is one of my favorite devices, especially for pentesting and ethical hacking.
The first Pi that I bought was a 3B+ and it worked as a great alternative to a virtual machine and provided a nice, responsive desktop machine.
I recently sprung for a the Raspberry Pi 4 with 8GB of RAM and it is really speedy as a Kali box. Since upgrading, I decided to use my 3B+ solely as a network hacking device since it had an Ethernet port and onboard Wifi.
Today, I am going to show you how to set up a rouge access point on your Pi with simple script and make it ready for deployment.
The Devices
NetGear EX2700 Wifi Range Extender
For this demonstration, we have several devices that we are going to use. The first is a simple NetGear Wifi Extender.
The NetGear EX2700 Wifi Range Extender was just something I had laying around the house, but it had an Ethernet Port on it so it made this perfect for my demonstration.
This is pretty handy wifi extender with really great range. I recently tested it against the WPS attack on Wifite2 and a few other wifi attacks. It passed all tests!
Raspberry Pi 3B+
The Raspberry Pi 3B+ has a ton of punch for such a small size.
While this isn’t the most powerful of the Pi line, it definitely has the power to get the job done.
I purchased this model from Amazon and got the official case for right around 50 bucks a couple of years ago. This is a great, inexpensive alternative to the Pi 4 and is really effective as a rouge AP and network hacking device.
Retractable Ethernet Cord
This has become one of the most useful tools in my pentesting kit.
Since this cable retracts into itself it makes cable management a breeze. I bought a pack of two Retractable Ethernet Cables on Amazon for about 10 bucks and keep them in my bag at all times.
TP-Link TL-WN722N v3
This has got to be one of the most famous wifi adapters out there.
While the version 1 WN722N was known for being a plug and play device for Kali, the TP Link WN722N v3 is plug and play with Raspberry Pi, Parrot and a few other distros. It’s also super cheap on Amazon at just 14.99. I have installed the wifi driver for this on Kali and also got it working on there.
For this demonstration, the V3 is plug and play with Raspian and works well with the script we are going to use. This is not essential for the demonstration, but it will increase the range and power of your rouge AP (you can also use any other monitor mode enabled wifi adapter).
Setting Up Your Rouge AP
There are a ton of tutorials on how to set up your Raspberry Pi so I won’t go into flashing the SD card or updating your software. The only thing we need to do is enable SSH so we can control the Pi remotely. Log into your pi and use the below command to enable SSH.
systemctl enable ssh
systemctl start ssh
If you followed my Building The Ultimate Portable Hacking Suite With A Raspberry Pi Zero W post then you will be familiar with the next script.
RPIHotspot allows you to create a wifi access point on your Raspberry Pi while also utilizing the internet connection on wlan0. Git clone into the link below to grab the hotspot script.
git clone https://github.com/idev1/rpihotspot.git
Go into the rpihotspot directory and make the set-up script executable.
chmod +x setup-network.sh
Now you want to run the set-up script. Its long so go into the rpihotspot directory and paste this in.
./setup-network.sh — install — ap-ssid=”RPIHoneypot” — ap-password=”raspberry” — ap-country-code=”US” — ap-ip-address=”10.1.1.1" — wifi-interface=”wlan0"
If you want to change the SSID you can change it here or you can just going to your hostapd.conf file to change it later. Same goes for the password.
If you want to use a different network adapter, such as the TP-Link adapter, change the interface name on the script to “wlan1,” or whatever interface name is given in ifconfig.
When you run the set-up script, you will need to reboot. Once you reboot you will see your SSID pop up on the wifi networks list. Connect to it. When you are connected to the hotspot’s SSID, you should be able to SSH into the Pi at 10.1.1.1.
From here, you can start to configure the hacking packages that you want. I have Metasploit, Recon-NG, hydra, crunch, cewl, Empire and a bunch of others installed.
Many people will ask why I haven’t used the Kali distro as my OS for the Pi. The reason is that it’s a nightmare to get hostapd working with NetworkManager. Raspian is so much easier.
Connecting To The Network
As you can see, all you have to do is connect your pi to a router or network device with an Ethernet port.
Once you have connected it to the port, you will be able to connect to your Pi over it’s rouge AP and start pentesting the devices connected to the network.
In this demonstration, I have a Ubuntu virtual machine connected to the network via the NetGear range extender.
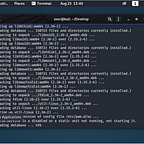
As you can see from the screenshot above, this virtual machine is connected at 192.168.1.212. I have SSH’d into my Pi via my ParrotSec VM (I rarely get to use it) and we’ll do a quick “pentest” on it.
A quick Nmap scan reveals that SSH is open. Let’s run Hydra and see if we get lucky!
Wow, this is one unsecured VM!
Why Would You Need This?
A dedicated rogue AP is something that all pentesters have in their arsenal. If you’re on an engagement and have the chance to quickly plug a Pi into a switch or router, you can instantly get on the network and start scanning clients.
But a rogue AP can be useful at home also. Even though my rouge AP is loaded with pentesting software, it is still an access point. Many people use this setup as a type of wifi extender. Of course this is also a great device for auditing your own network.
One problem is the issue of a power source. When on an engagement, you will not want to deal with finding an outlet to plug your pi into. One solution is use either the PiZ Uptime 2 or the Pi Sugar. Both of these offer battery power to the pi so you won’t have to worry about power.
If you liked this post and want more, follow me on here or give me a shout on Twitter @assume_breach